Take control of your Cyber Security and keep hackers out
Choosing the right security setup is all about finding a level that matches your organisation's size, risk profile and IT infrastructure.
Having the right protection will make it easier for you to focus on delivering your core business to customers.
Meanwhile, we keep the hackers out.
Choose the right approach to enhance your organisation's cyber security
There's no single approach that ensures security across your organisation's many activities. So where do you start and end? The answer depends on your organisation's IT infrastructure, size and work processes, among other things.
We offer services that are carefully designed to help your organisation exactly where you are on your maturity journey.
Maturity Assesment
Is your company ready for a cyberattack – or exposed by hidden vulnerabilities?
Cyber Review
Cybersecurity is a challenge for SMEs. We give you clarity today and stronger protection tomorrow.
Penetration Test
How much damage could a hacker do if they gained access to your internal infrastructure? Test your defenses.
Security partner
Are you prepared for the next cyberattack? Get advice and sparring from a dedicated security partner.
Read moreIncident Response
Do you know how to respond if a cyberattack hits? Get help with fast and effective incident handling.
NIS2 GAP analysis
Is your company ready to meet the new NIS2 requirements? Get an overview and be prepared before 2025.
2 specialised units of Cyber Security
In our Cyber Security area, we have two specialised departments: Cyber Defence Center and Security Consultancy.
In the Cyber Defence Center, we develop and offer a wide range of managed services within IT security – including SOC (Security Operations Centre).
Security Consultancy is based on your maturity level and helps you on your cyber security journey based on our framework. The framework is inspired by the NIST Cyber Security Framework developed by the National of Standards and Technology.
.jpg?width=600&height=600&name=Design%20uden%20navn%20(19).jpg)
Incident Response
Respond effectively to a cyber attack – or a suspected compromise of your organisation
If your organisation is hit by a hacker attack, it's important to respond quickly and correctly. The longer malicious hackers have access to your systems, the greater the impact it can have on your business.
Our team of experienced incident responders can provide professional help to get your business back to normal - efficiently and professionally.
Cyber Defence Center
Get one step ahead of cyber threats and protect your organisation
In today's complex threat landscape, traditional security measures are no longer enough. Hackers never take a day off, so your IT security needs to be awake around the clock – all year round.
At Cyber Defence Center, we specialise in monitoring and responding to cyber security incidents. Most of this is based on our SOC (Security Operations Centre).
With SOC and SOS (Security Operations Suite), you can stay one step ahead of cyber threats and protect your organisation with a combination of advanced technologies and expertise.

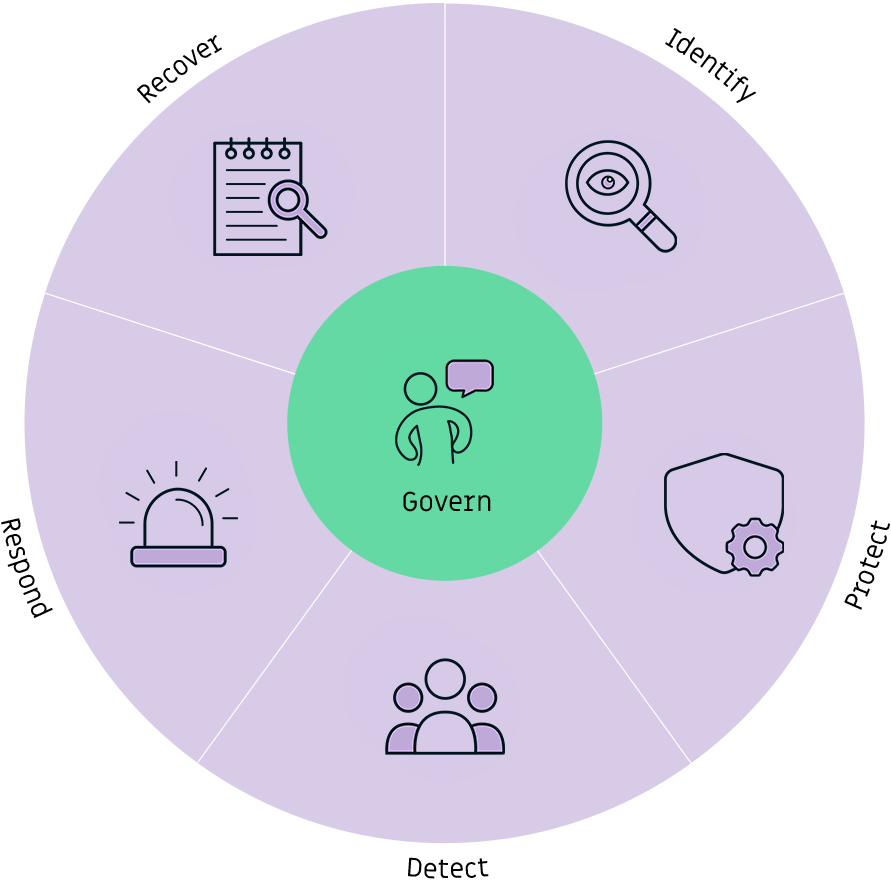
Identify
We identify security risks through an understanding of your business context, systems, data and threats.
Protect
We implement measures to ensure critical services remain operational in the event of a security breach.
Detect
We launch activities that detect threats and security breaches should they occur.
Respond
We develop actions to effectively handle the detected data breach in your organisation.
Recover
We establish resilient measures to restore capacity and ensure your organisation's continuity.
Govern
We monitor your organisation's strategy and expectations and the policies that manage your security risks.
Send secure email with SEPO
SEPO is more than just encryption – it's a powerful email tool that combines ease of use, scalability, and compliance. The solution automatically encrypts and decrypts your emails using OCES certificates, allowing you to send and receive sensitive data securely.
Whether you're communicating with authorities, citizens, customers, or partners, SEPO provides a proven and reliable solution for secure email – without compromising on flexibility or functionality.

Sign up for our Danish cyber newsletter
Want us to keep you updated with IT security news, tips and events?
Solid experience with
counselling of Danish
companies
Choosing the right security setup is about finding a level that matches your employees, risk profile and IT infrastructure.
For more than 15 years, we have advised customers on IT security within: Strategy, analysis, testing, software, training, monitoring and investigation.
This means we've helped dozens of organisations improve their IT security and acted as their trusted security partner.















A hacker attack can be an expensive experience. That's why you should prepare yourself for the attack that might hit you one day.
-1.jpg?width=600&height=600&name=Design%20uden%20navn%20(18)-1.jpg)
Identify
Strengthen your cyber security: Why it's important to know the security level of your business
You can't solve a problem you don't know about. Similarly, you can't patch the holes in a security net if you don't first understand the size, locations and number of holes.
Identifying threats and vulnerabilities in your IT infrastructure is a proactive way to protect your organisation against cyber attacks. It's a way to create a strong foundation for security because it allows you to take action where the risk is highest and the value is greatest.
We can help you identify threats and improve your security.